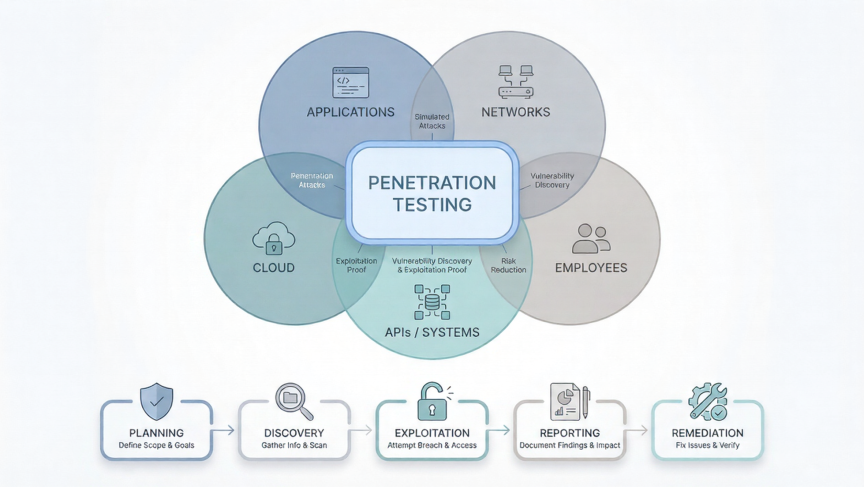
What Is Penetration Testing? The Methodology of Pentesting
Modern cyber threats increasingly target organisations through weaknesses in applications, networks, cloud environments, and employee behaviour. To stay ahead of these risks, security teams rely on penetration testing, also known as pen testing or pentesting. This article explains what penetration testing is, the methodology of pentesting, the steps of a penetration test, and the different […]
- Penetration Testing
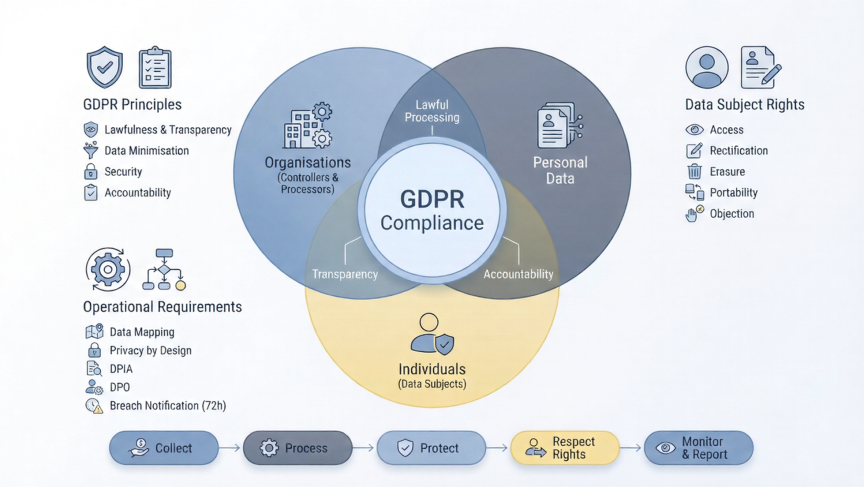
An Overview of GDPR Compliance: What It Is and Requirements
The General Data Protection Regulation (GDPR) is one of the most influential and far-reaching data privacy laws in the world. Since coming into effect on 25 May 2018, it has reshaped how organisations handle personal data, strengthened privacy rights across the European Union (EU), and raised global expectations for transparency, accountability, and security. This article […]
- Compliance
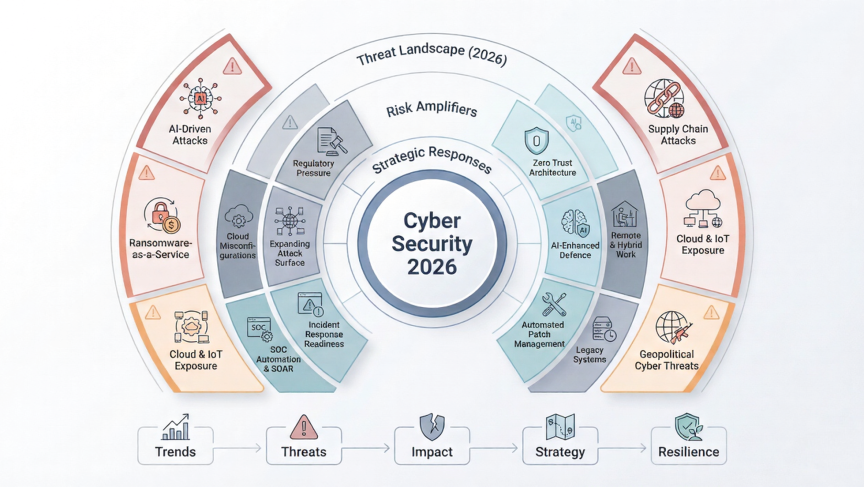
Cyber Security Trends, Threats, and Strategies for 2026
The cyber security landscape is shifting faster than ever. With attackers innovating at unprecedented speed and organisations depending heavily on distributed digital systems, understanding emerging cyber security trends, computer security trends, and wider IT security industry trends is no longer optional. It is fundamental to business survival. In 2026, the future of cyber security will […]
- Security Assurance