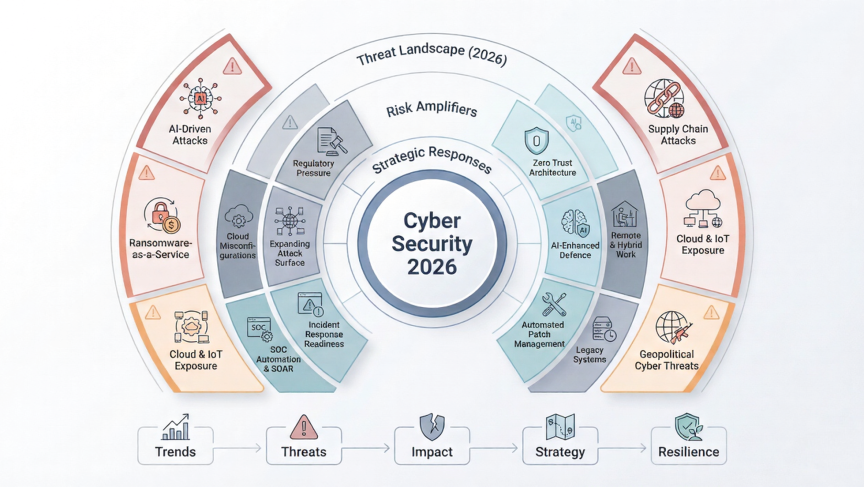
The cyber security landscape is shifting faster than ever. With attackers innovating at unprecedented speed and organisations depending heavily on distributed digital systems, understanding emerging cyber security trends, computer security trends, and wider IT security industry trends is no longer optional. It is fundamental to business survival.
In 2026, the future of cyber security will be shaped by a combination of AI-accelerated threats, geopolitical tension, the expansion of cloud and IoT ecosystems, and increasing regulatory pressure. This article explores the most significant cyber security technology trends, threats, and strategic responses every organisation must prepare for.
I. The Evolving 2026 Threat Landscape
What Cyber Security Trends Mean Today
Cyber security trends represent the ongoing shifts in attacker tactics, security technologies, and the global context. Staying ahead of these developments is critical. Failing to adapt leaves organisations vulnerable to financial loss, operational disruption, and long-term reputational damage.
In 2026, cybercrime’s financial impact is projected to position it as the world’s third-largest economy, surpassed only by the United States and China. This illustrates the scale of the challenge facing both private and public sectors.
Key Metrics Driving Today’s Risk Profile
- Vulnerabilities are accelerating: Over 30,000 vulnerabilities were disclosed last year, a 17% increase from previous totals.
- Cybersecurity investment is rising: IT spending reached 5.1 trillion dollars in 2024, with 80% of CIOs increasing security budgets.
- Remote and hybrid work continues: Home networks remain less secure than corporate environments, creating more opportunities for phishing, account takeover, and data exfiltration.
- Cloud adoption continues to expand: Misconfigurations remain a leading cause of large-scale breaches.
Traditional Defences Are No Longer Sufficient
Legacy tools struggle against fileless malware, multi-stage campaigns, and AI-powered social engineering. Many organisations rely on systems developed decades ago, which were not designed to address the decentralised, automated threat landscape that exists today.
II. Major Cyber Security Trends and Threats for 2026
The Weaponisation of Artificial Intelligence
Artificial intelligence is reshaping both offensive and defensive cyber operations.
1. Agentic Cyberattack and Defence
AI agents now automate reconnaissance, vulnerability identification, and intrusion actions, significantly reducing the skill level required to launch high-impact attacks.
2. AI-Driven Malware
Machine-learning malware can:
- Mutate and evolve in real time
- Evade static detection
- Modify behaviour dynamically
- Deploy automated zero-day exploitation
3. Deepfake and Synthetic Social Engineering
Deepfake social engineering is rapidly rising as a major cyber security trend. This includes:
- AI-generated executive voices
- Synthetic videos authorising payments
- False media used to create trust
4. AI-Powered Phishing
Highly personalised phishing campaigns are crafted with AI, making them significantly more convincing than traditional templates.
The Evolution of Ransomware
Ransomware continues to dominate as one of the most significant global cyber threats.
1. Ransomware-as-a-Service (RaaS)
Cybercriminal groups now operate like commercial service providers, offering:
- Attack kits
- Affiliate programmes
- Technical support
- Continuous updates
This model significantly broadens the range of individuals who can deploy ransomware.
2. Financial Impact
The average recovery cost following a ransomware attack is 2.73 million dollars, excluding longer-term reputational damage.
3. Exploitation of Known Vulnerabilities
Many ransomware incidents arise from vulnerabilities with available patches, highlighting the importance of automated updates.
Infrastructure, IoT, and Supply Chain Vulnerabilities
1. Supply Chain Attacks
Campaigns similar to SolarWinds demonstrate how compromising a single vendor can affect hundreds of downstream organisations.
2. IoT Device Expansion
In 2026, the world will have approximately 64 billion IoT devices. Many continue to lack:
- Strong encryption
- Updated firmware
- Reliable patching processes
One compromised device can provide attackers with access to core networks.
3. Cloud Container and Microservice Risks
Fast-paced DevOps environments introduce risks when container images are unpatched or misconfigured, enabling lateral movement inside cloud environments.
4. 5G and Edge Computing Risks
The growth of 5G and edge computing increases real-time data flows and expands the number of potential attack points.
Long-Term and Geopolitical Threats
1. Quantum Security Concerns
Nation-states may be collecting encrypted data today in the hope of decrypting it later when quantum computing becomes more accessible.
2. Escalating Global Cyberwarfare
Critical infrastructure, government institutions, and major corporations remain high-value targets in politically motivated cyber operations.
3. New and Re-Emerging Threat Actors
Modern cybercriminal groups benefit from automation, AI, and global distribution, enabling more frequent and more sophisticated attacks.
III. Strategies for Achieving Cyber Resilience in 2026
Zero Trust and Architectural Modernisation
1. Zero Trust Architectures (ZTA)
Zero Trust continues to be one of the most important Trend Micro Internet Security practices for 2026. It enforces:
- Continuous verification
- Micro-segmentation
- Context-based access
- Least-privilege policies
2. Real-Time Encryption and Segmentation
These measures help reduce breach impact and contain attacker movement.
3. IT and OT Convergence
As operational technology merges with IT systems, organisations require specialised monitoring and control mechanisms to avoid production disruptions.
Advanced Defensive Technologies
1. AI-Enhanced Threat Hunting
Artificial intelligence accelerates:
- Log analysis
- Anomaly detection
- Threat prediction
2. Explainable AI (XAI)
Security leaders increasingly require transparent AI systems that can justify decisions in real time.
3. Automated Patch Management
Given the rise in vulnerabilities, automation is essential to maintain consistent patching hygiene.
4. SOC Automation and SOAR
Automating high-volume tasks allows human analysts to focus on complex and high-risk incidents.
Strengthening the Human Layer and Governance
1. Continuous Security Training
Regular awareness training helps staff recognise phishing attempts and suspicious behaviour.
2. Identity and Access Management 2.0
Modern systems include:
- Biometric authentication
- Continuous session validation
- Passwordless login
- Automated role provisioning
3. Data Privacy and Governance
Regulations such as GDPR and HIPAA demand strict access controls and comprehensive privacy strategies.
4. Business-Aligned Security
Security leaders are shifting towards programmes that balance operational needs with risk reduction.
Continuous Improvement and Response Readiness
1. Regulatory Evolution
Cybersecurity legislation across regions is becoming stricter and broader in scope.
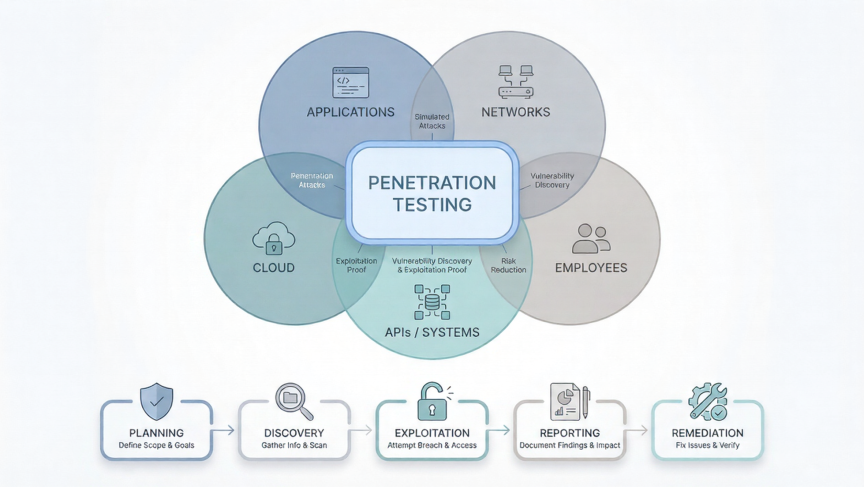
2. Frequent Risk Assessments
Routine vulnerability scanning, penetration testing, and attack-surface monitoring are now essential.
3. Secure-by-Design
Embedding security into product and software development reduces long-term cost and strengthens resilience.
4. Incident Response Preparedness
Organisations require rehearsed, clearly defined IR plans for ransomware incidents, supply chain compromise, and cloud-based attacks.
IV. Industry-Specific Risk Profiles
Healthcare
- High-value patient data
- Average breach cost of 9.77 million dollars
- Requirements: encryption, segmentation, Zero Trust
Financial Services
- High exposure to fraud, account takeover, and phishing
- Strict regulatory requirements such as PCI DSS and PSD2
Manufacturing and Industrial IoT
- IT and OT environments merging
- Requires OT security controls, regular patch cycles, and segmentation
Government and Public Sector
- Large volumes of citizen data
- Often reliant on legacy systems
- Requires urgent modernisation and training investment
The future of cyber security in 2026 will be defined by artificial intelligence, automation, and unprecedented digital complexity. Attackers are evolving rapidly, targeting cloud environments, supply chains, identity systems, and the human layer with increasing sophistication.
To remain resilient, organisations must adopt modern architectures, intelligent automation, Zero Trust principles, and continuous assessment. Cyber resilience is no longer a technical requirement. It is a strategic business imperative.
SeCore supports organisations by providing the visibility, measurement, and continuous improvement capabilities required to outpace evolving threats and build lasting resilience. If you want to explore more, follow through the penetration testing & security assurance services.