The General Data Protection Regulation (GDPR) is one of the most influential and far-reaching data privacy laws in the world. Since coming into effect on 25 May 2018, it has reshaped how organisations handle personal data, strengthened privacy rights across the European Union (EU), and raised global expectations for transparency, accountability, and security.
This article provides a complete GDPR overview, explaining what GDPR is, what GDPR stands for, the purpose of GDPR, the core GDPR requirements, and what it means for an organisation to be GDPR compliant.
I. Introduction to GDPR
What Is GDPR? (General Data Protection Regulation Overview)
The General Data Protection Regulation (GDPR) is a comprehensive data protection regulation enforced across the EU. It replaced the 1995 Data Protection Directive and became legally binding on 25 May 2018.
What does GDPR stand for?
GDPR stands for the General Data Protection Regulation.
GDPR Law Background
It is widely regarded as the strongest privacy law globally, setting strict rules on how organisations collect, store, process, and protect personal data.
Purpose of GDPR
The regulation aims to:
- Protect the personal data of individuals in the EU.
- Give people greater control over their personal information online.
- Establish consistent data privacy compliance standards across all EU member states.
- Clarify how organisations may lawfully collect, use, share, and retain personal data.
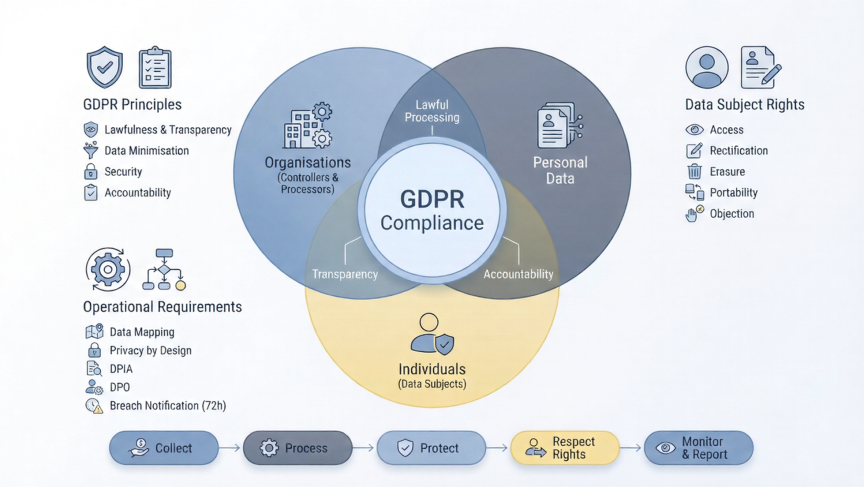
GDPR Compliance
GDPR compliance refers to meeting all requirements outlined in the regulation, including security, lawful processing, transparency, and respecting individual rights.
What does it mean to be GDPR compliant?
An organisation is considered compliant when it:
- Collects and processes personal data securely.
- Has a lawful basis for all processing.
- Is transparent about its data practices.
- Respects all GDPR rights granted to individuals.
- Implements appropriate technical and organisational measures.
This is the core meaning of GDPR compliance definition.
II. Scope and Applicability of GDPR Regulations
Extraterritorial Scope
The General Data Protection Regulation 2018 applies to:
- All organisations operating within the EU.
- Non-EU organisations that offer goods or services to EU residents.
- Companies that monitor the behaviour of EU users (such as via online tracking).
This broad scope ensures that GDPR has a global impact.
Key Parties Defined by GDPR
GDPR identifies several important roles:
Data Subjects
Individuals whose personal data is collected or processed.
Data Controllers
Entities that decide how and why personal data is processed. They carry primary responsibility for compliance with GDPR regulations.
Data Processors
Third parties who process data on behalf of controllers, such as cloud platforms, analytics tools, or payment providers.
Personal Data
Any information relating to an identifiable person, including:
- Name, email address, home address
- IP address
- Biometric data
- Cookie identifiers
III. Core Principles and Requirements of GDPR
The Seven Principles of GDPR
These foundational rules guide all processing activities:
- Lawfulness, fairness, and transparency
- Purpose limitation
- Data minimisation
- Accuracy
- Storage limitation
- Integrity and confidentiality (security)
- Accountability
Organisations must document and demonstrate compliance with all seven principles.
Lawfulness of Processing and Consent
Processing personal data requires a lawful basis, such as:
- Consent
- Contract
- Legal obligation
- Vital interests
- Public task
- Legitimate interests
Consent Requirements under GDPR
Valid consent must be:
- Freely given
- Specific
- Informed
- Unambiguous
- Given through a clear affirmative action
Individuals must also be able to withdraw consent easily.
Special Categories of Data
These include sensitive data such as:
- Health information
- Genetic and biometric data
- Data revealing racial or ethnic origin
Processing such data usually requires explicit consent or another valid exemption.
IV. Data Subject Rights under GDPR
GDPR grants individuals extensive control over their personal data.
1. Right to be informed
Transparency about how data is collected and used.
2. Right of access
Individuals can request copies of their data.
3. Right to rectification
The right to correct inaccurate or incomplete information.
4. Right to erasure (Right to be forgotten)
Data subjects may request deletion of data under certain conditions.
5. Right to restrict processing
Processing may be limited while accuracy or legality is investigated.
6. Right to data portability
Personal data must be provided in a machine-readable format for transfer to another controller.
7. Right to object
Individuals can object to processing, particularly for direct marketing.
8. Right to withdraw consent
Consent can be revoked at any time.
Organisations must respond to requests within one month, typically via a DSAR (Data Subject Access Request) process.
V. GDPR Compliance Requirements: Operational Practices
Core Data Management Requirements
1. Data Audit and Mapping
Organisations must understand:
- What data they collect
- Why they collect it
- Where it is stored
- Who accesses it
Data mapping is essential for transparency and risk identification.
2. Data Protection by Design and Default
Privacy must be integrated into systems, processes, and infrastructure from the very beginning.
3. Data Protection Impact Assessments (DPIAs)
Required for high-risk activities to prevent harm before processing occurs.
4. Data Protection Officer (DPO)
Some organisations must appoint a DPO to:
- Oversee privacy strategy
- Monitor compliance
- Liaise with supervisory authorities
5. Reviewing Third-Party Processors
Controllers must ensure processors follow GDPR requirements and must have a Data Processing Agreement (DPA) in place.
International Data Transfers
Transfers outside the EEA require safeguards such as:
- Standard Contractual Clauses (SCCs)
- Binding Corporate Rules (BCRs)
- Adequacy decisions
Website and Privacy Notice Compliance
Privacy Notice Requirements
A GDPR-compliant privacy notice must include:
- What data is collected
- The lawful basis
- How long data is retained
- Who data is shared with
- User rights
GDPR Website Compliance and Cookie Compliance
Key requirements include:
- A cookie banner for non-essential cookies
- Blocking non-essential cookies until consent is given
- Equal Accept and Reject options
- Granular cookie settings
- HTTPS encryption
This is the essence of GDPR cookie compliance and cookie compliance more broadly.
Breach Detection and Response
Organisations must:
- Detect incidents promptly
- Notify the supervisory authority within 72 hours
- Notify affected individuals if there is high risk to their rights
VI. Enforcement and Support
Penalties for Non-Compliance
GDPR penalties can reach:
- €20 million, or
- 4 percent of global annual turnover
whichever is higher.
Enforcement and Compliance Tools
National Data Protection Authorities (DPAs) enforce GDPR locally.
Organisations may use tools such as:
- CookieYes
- OneTrust
- Microsoft Purview
- Other privacy automation solutions
These assist with assessments, cookie consent management, data mapping, and incident reporting.
VII. Understanding GDPR Compliance
Think of GDPR compliance as a meticulous librarian who handles rare, sensitive documents. The librarian:
- Knows where each document is stored
- Ensures only authorised people can see it
- Allows the owner to correct or remove it
- Protects it with strong security
Failure to follow these rules results in severe consequences from the Library Board, much like GDPR supervisory authorities.
GDPR is more than a regulation. It is a comprehensive framework that ensures fairness, transparency, accountability, and respect for individual rights in the digital age. Achieving GDPR compliance requires clear governance, privacy-by-design principles, strong security controls, and a proactive approach to data management.
SeCore supports organisations in navigating GDPR compliance requirements, mapping risks, strengthening data protection processes, and building trust with customers and regulators alike. If you want to explore more, simply follow the expert-led penetration testing services and continuous security assurance.