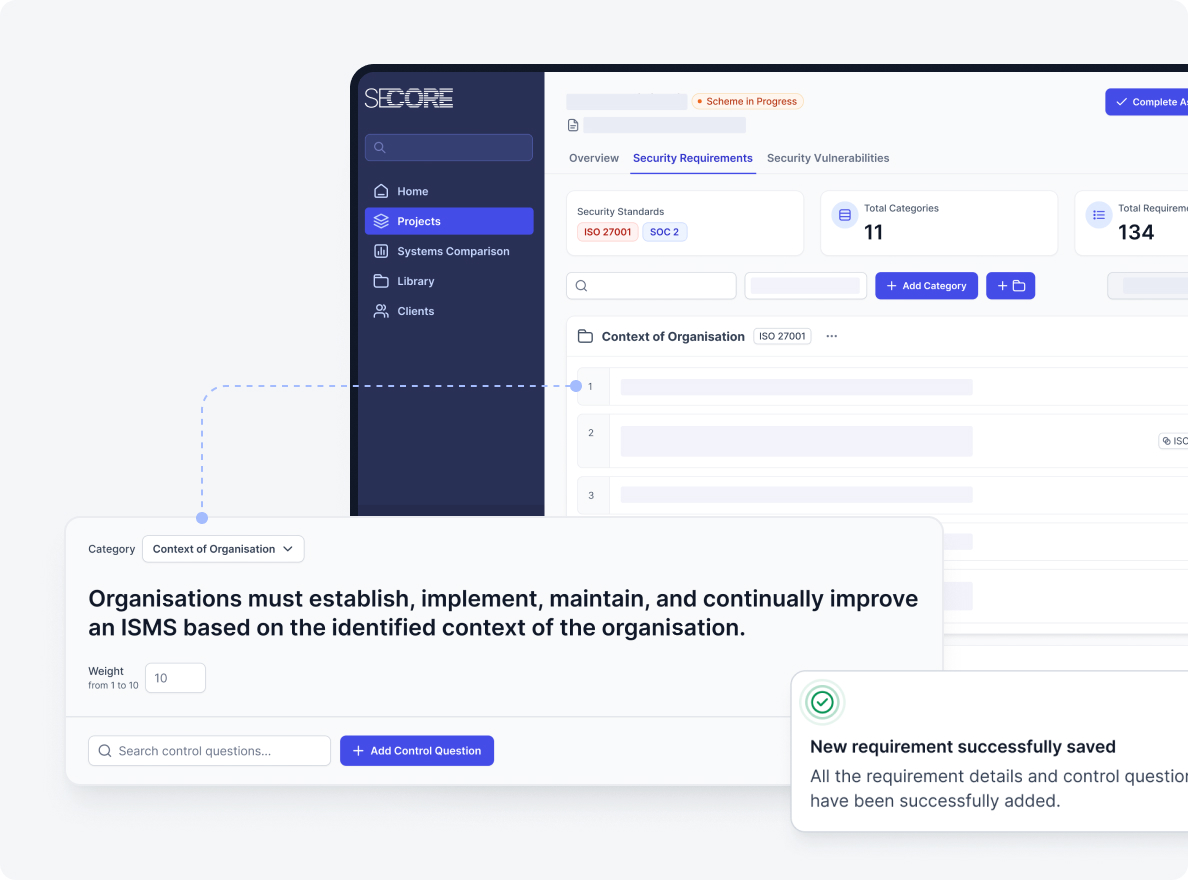
Specify a Security Assurance Profile
This initial step involves defining the scope and context of the security assurance engagement. It is crucial to establish a clear understanding of what needs to be assured, against what criteria, and for what purpose. This phase sets the foundation for all subsequent activities, ensuring that the evaluation is aligned with organisational objectives and regulatory requirements.
- Identify the Assurance Target: Clearly define the system, application, or environment that will be subjected to security assurance.
- Select Applicable Standards and Frameworks: Determine which industry standards, regulatory frameworks, and internal policies are relevant.
- Define Organisational Risk Tolerance: Understand the organisation’s appetite for risk.
- Establish Business Context and Objectives: Link the security assurance efforts directly to business outcomes.
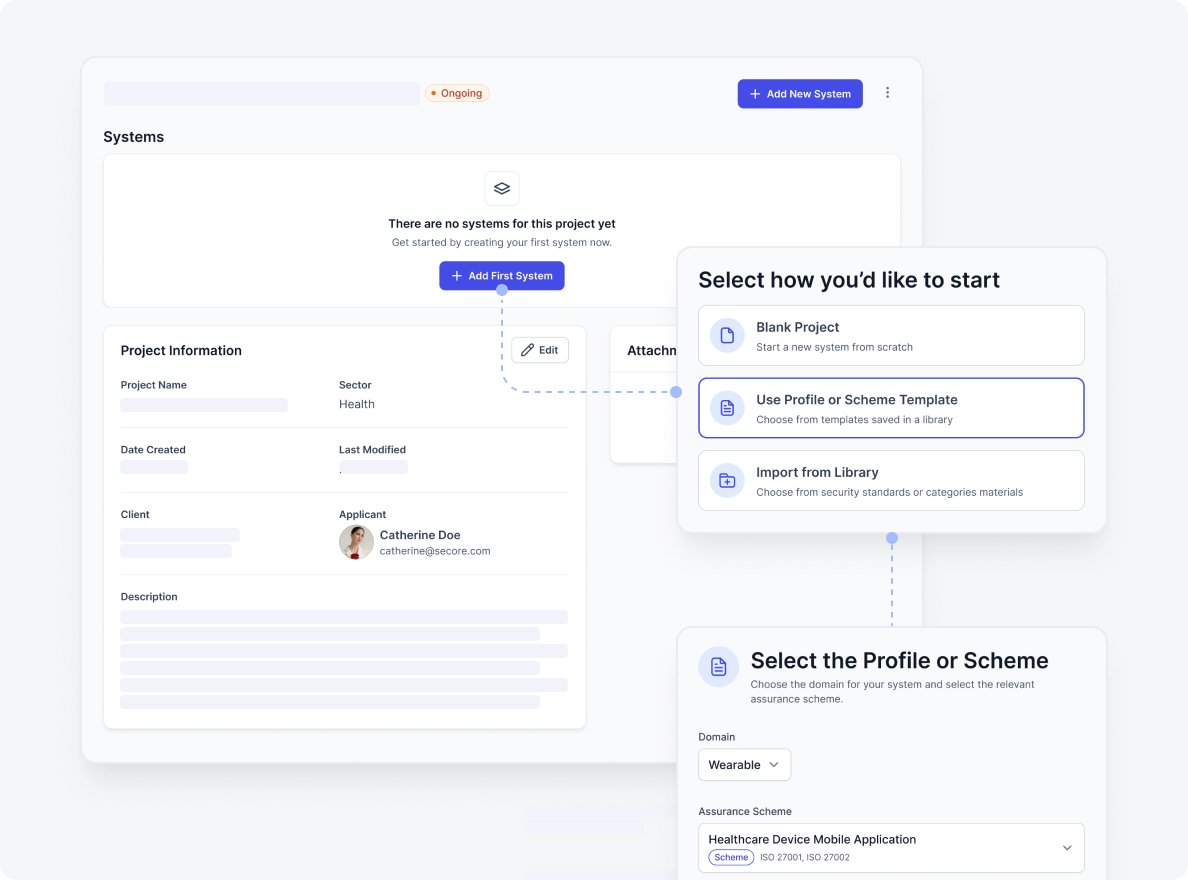
Specify Your System of Evaluation
Once the security assurance profile is defined, the next step is to detail the specific components and elements within the assurance target that will be evaluated.
- Decompose the System into Components: Identify all relevant components of the system under evaluation.
- Map Components to Assurance Criteria: Relate each identified component to security domains.
- Identify Assurance Elements: Pinpoint specific elements to be assessed.
- Define Assurance Conditions: Specify concrete, testable security controls or conditions.
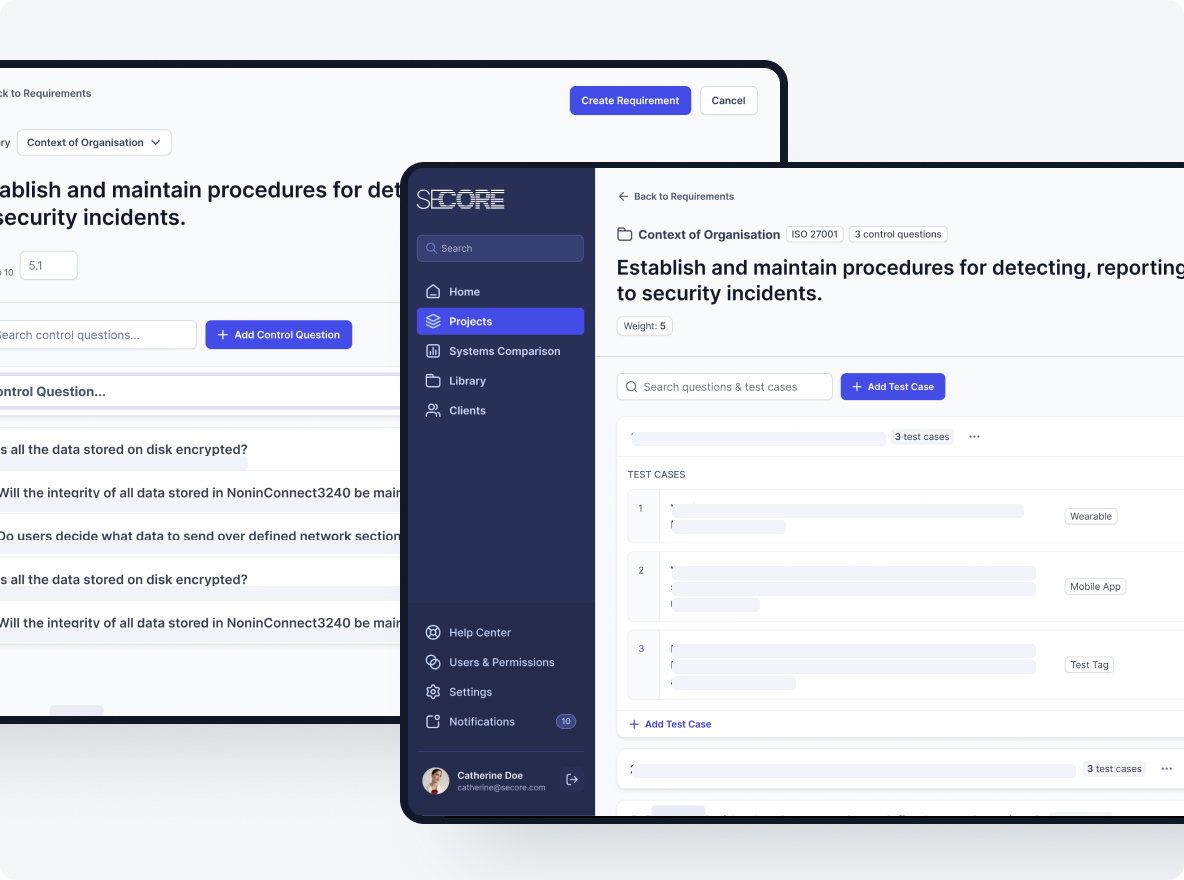
Create a Security Assurance Scheme and Test Plan
This phase translates the defined system components and assurance conditions into a structured evaluation plan.
- Map Criteria to Measurable Metrics: Assign numerical scores or indicators.
- Develop Test Cases and Procedures: Design detailed, repeatable, and objective tests.
- Assign Risk and Importance Weights: Prioritise based on organisational risk.
- Integrate with Existing Tools and Processes: Leverage existing security tools.
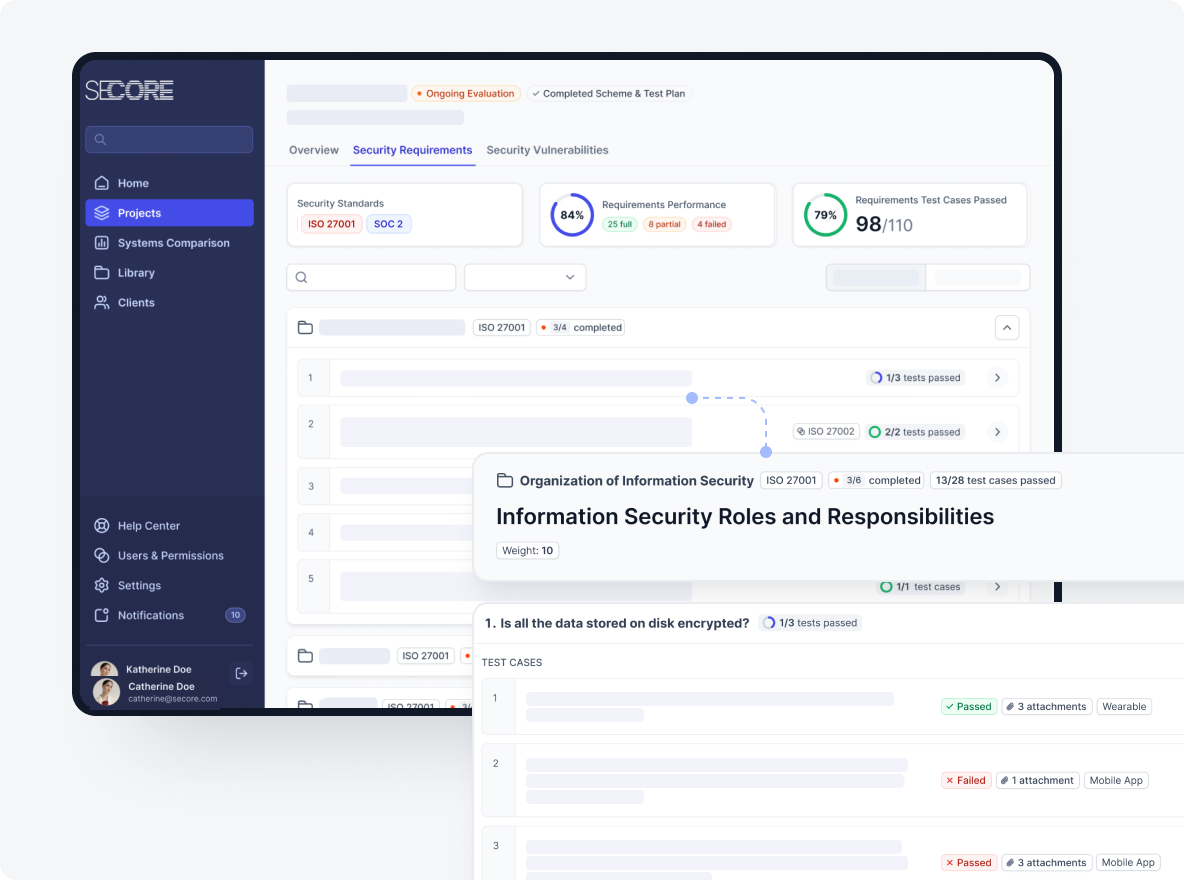
Conduct Evaluation
This is the execution phase where the defined test plan is put into action.
- Execute Test Cases: Perform tests as defined.
- Collect and Record Data: Gather relevant test results.
- Analyse Findings: Understand root causes and security weaknesses.
- Calculate Scores: Provide a quantitative measure of security posture.
Reporting
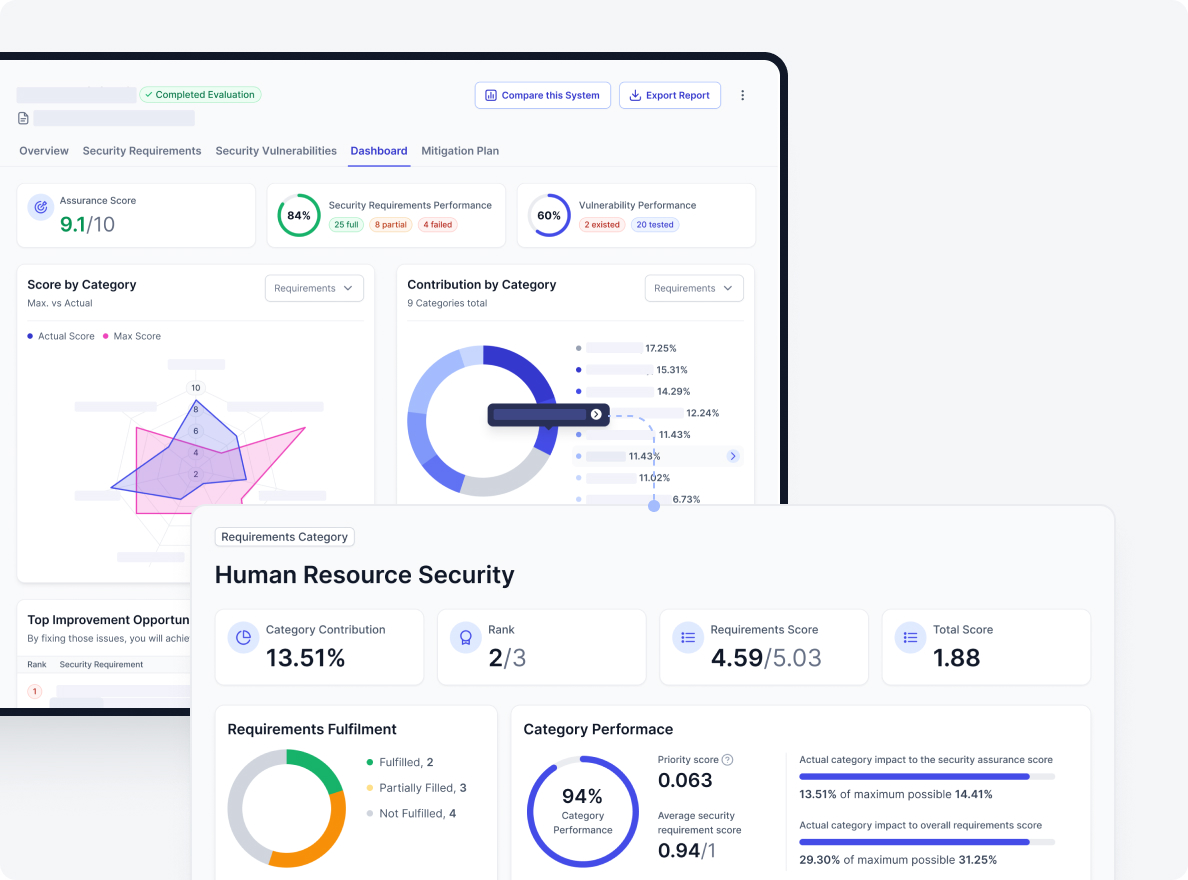
The reporting phase involves synthesising the evaluation findings into clear, concise, and actionable reports.
- Generate Comprehensive Reports: Present findings including SAL and VUP.
- Visualise Data: Use dashboards and charts.
- Translate Technical Findings to Business Impact: Link vulnerabilities to business consequences.
- Provide Actionable Recommendations: Offer clear, prioritised guidance.
Mitigation
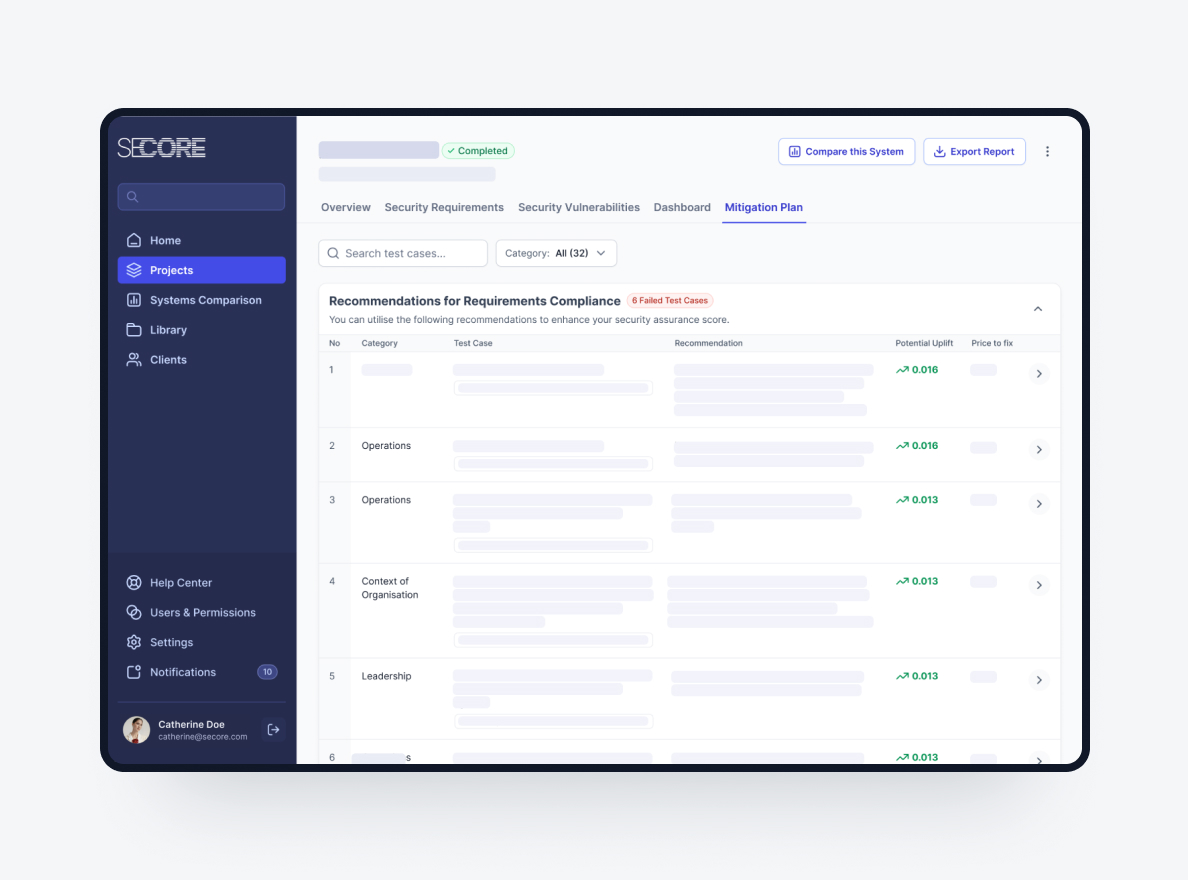
The final phase focuses on addressing identified weaknesses and improving security posture.
- Prioritise Mitigation Actions: Focus on high-risk areas first.
- Verify Effectiveness: Re-test to confirm improvements.
- Continuous Monitoring and Improvement: Track security posture over time.
FAQ
Ready for Security Evaluation with SeCore?
Cyber threats evolve fast, your defences should too. With SeCore’s Security Assurance Methodology, you gain clear visibility into your security posture, benchmarked across leading standards and best practices. Our expert-led evaluations deliver measurable insights, prioritised remediation plans, and a single security score you can trust. Contact SeCore today to schedule your security evaluation and strengthen your organisation’s resilience.
Get in Touch