Modern cyber threats increasingly target organisations through weaknesses in applications, networks, cloud environments, and employee behaviour. To stay ahead of these risks, security teams rely on penetration testing, also known as pen testing or pentesting. This article explains what penetration testing is, the methodology of pentesting, the steps of a penetration test, and the different types of pen testing used to identify vulnerabilities before attackers exploit them.
I. What Is Penetration Testing?
Penetration testing is an authorised, simulated cyberattack on a computer system, network, or application. Its goal is to identify weaknesses by replicating how a malicious attacker would attempt to breach the organisation.
Meaning of Penetration Testing
Pen testing is the practice of:
- Simulating real-world attacks
- Discovering vulnerabilities
- Demonstrating how attackers could exploit them
Security professionals who perform these tests are often referred to as ethical hackers.
Unlike automated scans, pen testers apply technical skill, creativity, and adversarial thinking to identify weaknesses that automated tools overlook.
Penetration Testing vs Vulnerability Scanning
While both activities identify security issues, they differ significantly:
| Vulnerability Scanning | Penetration Testing |
| Automated | Manual and automated |
| Broad overview | Deep, targeted examination |
| Identifies potential issues | Confirms real exploitable vulnerabilities |
| Lower cost | Higher depth, higher accuracy |
Penetration testing significantly reduces false positives because testers exploit vulnerabilities to prove they are real.
Scope of Penetration Testing Targets
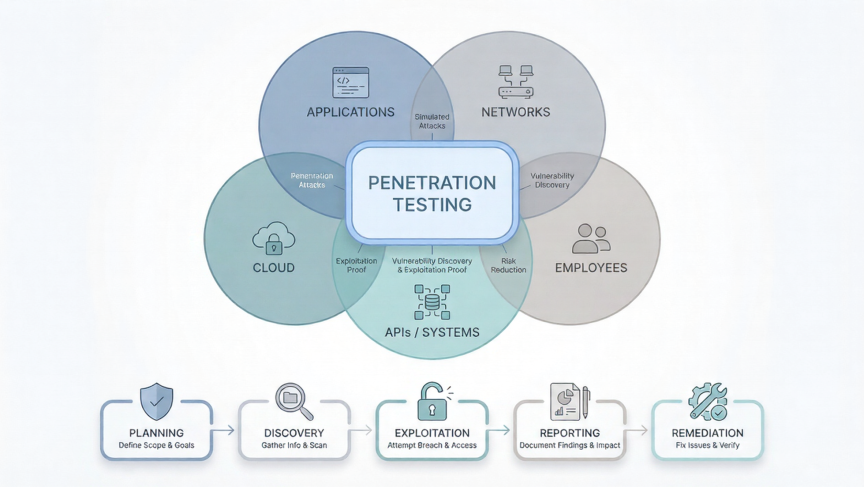
Penetration testing can be applied to many assets, including:
Web Applications
Testing authentication, injection flaws, broken access control, and insecure configurations.
Mobile Apps
Evaluating session management, authentication weaknesses, and insecure local data storage.
Network Penetration Testing
Examining:
- Encrypted transport protocols
- Weak network services
- Firewall misconfigurations
- Internal versus external attack surfaces
Cloud Systems
Assessing misconfigurations, identity and access management flaws, storage buckets, and shared responsibility gaps.
APIs
Testing for broken authorisation, excessive data exposure, weak rate limiting, and insecure endpoints.
Databases
Ensuring proper access control, encryption, and security configuration.
IoT and Embedded Devices
Identifying hardware and firmware weaknesses, insecure communication, and poor patching.
CI/CD Pipelines
Identifying issues in build processes, automation scripts, secrets management, and deployment workflows.
II. Importance and Benefits of Penetration Testing
Penetration testing provides an opportunity to see systems from a hacker’s perspective. It answers the critical question: What can an attacker actually achieve if they attempt to breach us?
Key Benefits of Penetration Testing
- Identify and prioritise security vulnerabilities
- Reduce the risk of breaches, downtime, and financial losses
- Understand the real impact of exploitation
- Strengthen weak controls before attackers exploit them
This is the core penetration testing purpose: preventing real incidents by discovering weaknesses in advance.
Operational and Strategic Advantages
Penetration testing provides:
1. Increased Confidence in Security
Regular testing improves confidence in defensive tools, processes, and monitoring systems.
2. Verification of Existing Security Measures
Penetration testing validates:
- Controls
- Policies
- Detection tools
- Security monitoring
3. Incident Response Evaluation
A covert test measures how quickly and effectively staff respond to suspicious activity.
4. Staff Awareness
Social engineering tests evaluate how employees react to phishing emails, impersonation attempts, and fraudulent instructions.
5. Intelligent Budget Allocation
Pentesting results highlight exactly where security investment is needed.
Compliance Requirements
Many regulatory frameworks mandate annual or periodic penetration testing, including:
- PCI DSS
- HIPAA
- GDPR
- SOC 2
- ISO 27001
Penetration testing helps organisations prove compliance with required security controls.
III. Pen-Testing Methodology and Phases
Pen testing methodologies include:
- PTES (Penetration Testing Execution Standard)
- NIST SP 800-115
- OWASP Testing Guide
While different frameworks exist, the penetration testing process usually follows the phases below.
Phase 1: Planning and Scoping
This stage defines:
- Objectives
- Scope
- Timeframes
- Targets
- Methodology
- Rules of engagement
It establishes whether the test will be:
- Black box (no information)
- White box (full information)
- Gray box (partial information)
Legal authorisation must be granted before testing begins.
Phase 2: Reconnaissance (Discovery)
Testers collect information through:
- Internet searches
- OSINT (Open Source Intelligence)
- Network scanning
- Cloud enumeration
- Public records
- Metadata analysis
The goal is to understand the system and identify potential attack paths.
Phase 3: Penetration and Exploitation
Testers attempt to exploit discovered vulnerabilities using techniques such as:
- SQL injection
- Cross-site scripting (XSS)
- Brute-force attacks
- Social engineering
- Denial-of-service attempts
- Man-in-the-middle attacks
The goal is to gain unauthorised access and demonstrate the real-world impact of a breach.
Phase 4: Escalation and Maintaining Access
Once access is obtained, testers attempt to:
- Escalate privileges
- Pivot across systems
- Maintain persistence
- Move laterally through the environment
This simulates how advanced threat actors behave.
Phase 5: Cleanup and Reporting
Testers remove:
- Backdoors
- Malware
- Added accounts
- Modified configurations
After cleanup, a detailed report is produced, including:
- Vulnerabilities found
- Exploitation steps
- Tools used
- Business impact
- Remediation guidance
Phase 6: Remediation and Re-testing
Organisations fix identified issues and request a re-test to confirm the vulnerabilities have been resolved.
Regular pentests should be carried out:
- Annually
- Quarterly (for high-risk environments)
- After major infrastructure changes
IV. Types of Penetration Testing
Knowledge-Based Testing Types
Black Box Testing
Simulates an external attacker with no prior knowledge.
White Box Testing
The tester receives full internal visibility, including:
- Credentials
- Architecture diagrams
- Source code
Gray Box Testing
The tester has partial knowledge, simulating an attacker with limited internal insight.
Specialised Testing Types
Social Engineering
Simulates phishing, impersonation, and physical intrusion.
Red Team and Blue Team Exercises
- Red Team: Attempts to breach systems
- Blue Team: Defends against attacks
- Purple Team: Collaborative approach to strengthen controls
Covert Pen Testing
Few staff members are aware of the test. This evaluates real-time detection and responsiveness.
AI and Large Language Model (LLM) Pen Testing
Assesses AI systems, model poisoning vulnerabilities, prompt injection risks, and misuse controls.
V. Tools and Execution
Automation in Penetration Testing
Pentesters use both manual techniques and automated penetration testing tools.
Automation assists with:
- Scanning
- Discovery
- Repetitive tasks
- Large-scale enumeration
However, manual testing remains essential for identifying complex vulnerabilities.
Categories of Pen Testing Tools
Specialised Operating Systems
- Kali Linux
- BlackArch
- BackBox
- Parrot OS
Vulnerability Scanners
- Nessus
- Core Impact
- OpenVAS
- OWASP ZAP
Exploitation Frameworks
- Metasploit
- Canvas
- Core Impact
Credential-Cracking Tools
- John the Ripper
- Hashcat
Reconnaissance Tools
- Nmap
- Wireshark
Hardware Tools
- Flipper Zero
- Proxmark3
- Raspberry Pi
- USB exploitation devices
Use of Exploits
Pentesters use exploits from:
- Public exploit libraries
- Certified exploit packs
- Custom-written scripts
They simulate realistic attack techniques used by cybercriminals.
Understanding Penetration Testing
Penetration testing is similar to hiring a skilled, authorised burglar to attempt breaking into your home. Unlike a surface-level inspection (a vulnerability scan), the ethical hacker:
- Tests every lock and window
- Searches for hidden weaknesses
- Demonstrates exactly what valuables they could access
- Provides a detailed report showing how to secure your property
This process ensures vulnerabilities are identified and fixed before a real attacker exploits them.
Penetration testing is a foundational component of cybersecurity strategy. It enables organisations to proactively identify weaknesses, measure the real impact of potential attacks, and strengthen their resilience. By following structured methodologies, performing regular tests, and using a combination of manual and automated tools, organisations can protect critical assets, improve incident readiness, and meet regulatory requirements.
SeCore helps organisations evaluate vulnerabilities, close security gaps, and build a stronger, more resilient security posture through structured, expert-led penetration testing services and continuous security measurement.